What do we mean by CIAM?
Customer Identity and Access Management (CIAM) is the term used to describe the solution applied by companies to provide end users with secure access to the digital services they offer. Digital services can include anything from e-commerce, cloud services, customer accounts, and beyond.
CIAM can be described as a blend of security and customer experience. It is a form of identity access management that protects customer privacy online and enhances digital security. In other words, CIAM provides an easy, frictionless way for users to log into digital services with their identity while protecting sensitive data correctly and complying with data privacy laws.
Customer Identity Is One Of Four "Identity Pillars"
Let’s begin by discussing what we mean by customer identity in the context of the four widely accepted pillars of CIAM. The pillars of CIAM describe the main areas where data security, user access, personal privacy, and identity management are needed in today's digital world.
The first pillar is personal identity. Workforce identity use our personal information to:
- get a driver's license or passport.
- interact with governments.
- to travel freely.
- submit a tax return.
The second pillar is workforce identity. It is used to access applications and software in the office and workplace.
The third pillar is specifically about devices - the Internet of Things. There are millions of devices coming online every day that require authentication, software, security, and other CIAM solutions.
The fourth pillar is customer identity - the customer information used for transactions online and other customer experiences.
People interact with these identities on a daily basis and want the reassurance that each identity is protected. This is where CIAM steps in to help. Customer identity management provides privacy and security solutions that protect customer identity and gives each user peace of mind.
What macro trends do we see today around CIAM solutions?
Let’s look at the macro digital trends that are impacting consumer behavior and increasing the need for CIAM solutions.
We already know the world we live in is a dynamic place, one that keeps evolving and is becoming more complex.
Complexity drives change, which leads to risk. Increased risk drives costs. There is a sharp increase in the number of technologies coming online very quickly, coupled with increased customer expectations.
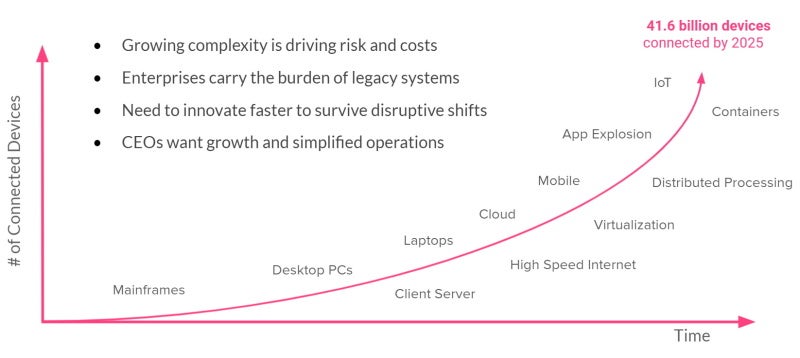
Some of these technologies include consumer devices like fridges, cars, and TVs with enhanced digital features.
But we're also seeing faster adoption of cloud technologies. And this means organisations have to innovate faster to grow and increase their performance while at the same time trying to simplify their solutions and operations. An increase in cloud technologies has also created a need for cloud identity management and security solutions.
These consumer trends have redefined everything we do with our workforce, our customers, and our CIAM solutions.
The “Amazon Effect” is felt across all sectors
Another trend we see is the workforce becoming more remote-based. Along with customers buying more things online.
The impact of companies like Amazon and Facebook is that every interaction that you have online can now be done from any device - your phone, your tablet, or even your laptop at work. Customers interact with their identity on each platform and on each device, which means that their personal information is spreading to more and more locations. And without proper security and privacy measures in place, hackers will have access to their information.
And when customers use an online site, they expect a smooth, personalized experience using the information they provide.
This increased expectation from consumers is felt across every sector, not just e-commerce, and it completely redefines customer engagement and management.
The Traditional CIAM Security Perimeter is gone
As customer expectations change and engagement increases, it redefines how we secure data and provide CIAM solutions.
- Previously, security models depended on architecture with the network and data center on the inside and firewalls guarding the perimeter.
- Anything on the inside was considered trusted.
- Anything located on the outside was considered untrusted.
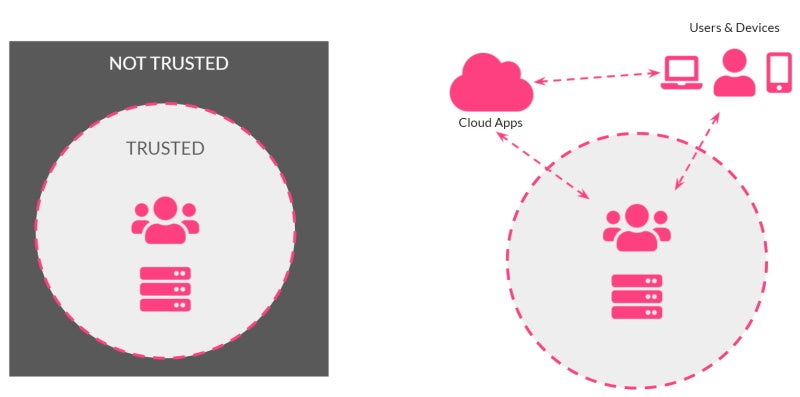
However, this trust breaks down when users are mobile and when external partners require access.
This is why we hear “zero trust” a lot these days - which is essentially a new approach where trust levels are continuously calculated and adapted to allow just-in-time, just-enough access to resources. The goal is to prevent users without authentication from gaining account access and allow users with authentication to access their accounts securely.
Compliance & Regulations
Recent customer trends have also influenced data management processes - and so compliance is a big issue surrounding CIAM solutions.

First of all, there is Data residency - where a business specifies that data is stored in a specific geographical location.
Then there is Data sovereignty, where the data is also subject to the laws of the country in which the information is physically stored.
The third, and fastest-growing trend, is Data localization. This requires that data created within certain borders stays within those borders.
Everything accelerated by the pandemic
A parallel challenge to CIAM compliance is the rate at which things and customer expectations have changed due to the pandemic.
Many consumers discovered the convenience of e-commerce and other online experiences during the pandemic. While shopping online, they want adequate access to customer support and a smooth user experience. In this chart, you can see the share of e-commerce grew at two to five times the rate of growth before COVID-19.
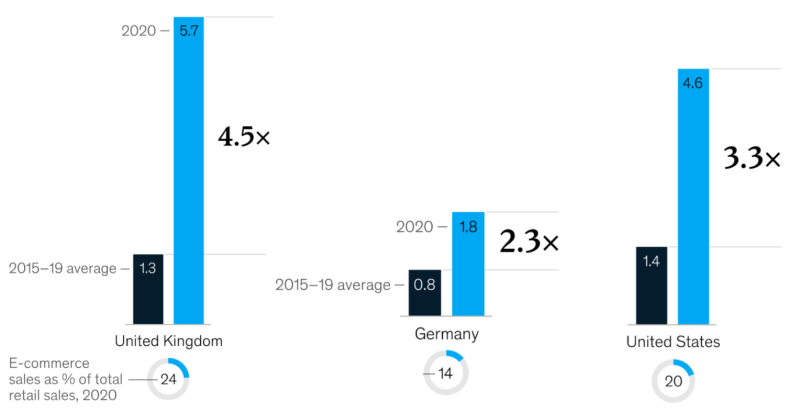
McKinsey tells us that roughly three-quarters of people using digital channels for the first time say they will continue using them when things return to “normal”.
There's another great report that McKinsey put out earlier this year (1), which showed the acceleration of technology and digital transformation, mainly driven via the pandemic. They highlighted two case studies. The first was all about workforce collaboration. Turnaround time was around 400 days before the pandemic and deliverables were emerging in under 2 weeks.
The second case study was around customer digital experiences. Organizations building apps were taking an average of around 450 days which was dropping to 29 days. So the deliverables were delivered in a single month.
How a CIAM solution will address these trends
With all these changes in the digital world, customer experience, and the workplace, there is a lot to keep up with. But CIAM solutions are able to provide the necessary support that makes it easy to adapt and stay up-to-date with security management.
Let's break down how a customer identity and access management solution can help you achieve your goals by summarizing the three keys of CIAM below;
- Create a unified 360-degree view of your customers' experiences from different datasets
- Improve the experience and reduce churn with frictionless authentication
- Maintain safety and security as data breaches increase
1. A unified 360 degree view for customer identity and access management
As mentioned earlier, identity management is not just a topic for Amazon or other retail organizations - it is of primary importance for any customer facing company. Offering the best customer service and support requires you to learn and develop a deep understanding of customer behaviour, experiences, and interests.
Identity as a service solutions, such as Okta, build profiles for each user, pulling in attributes and data from multiple sources to build up a "master profile." The user account in CIAM also tracks and manages login activity across different devices and sessions.
If social identity providers are included as an authentication option and the user chooses to use multiple sources such as Facebook, LinkedIn, and Google, the platform can link these accounts together, merging different sets of information.
Once you have assembled a unified view of your customers, the data can then be integrated with other tools such as CRM and Analytics platforms — this feeds the types of content your users can see and explore. It also gives customers a more personalized experience overall. Throughout this process, it is important to ensure privacy and security for your customers through CIAM solutions.
2. Frictionless login and registration
The cost and effort of switching services and platforms are very low these days. In addition, product reviews and complaints are commonplace, typically published via social media, aggregator sites, and search engines.
To mitigate user complaints this, aiming for a superior authentication experience for your users should be high on the agenda. Many companies still struggle with poor login or registration flows. Long forms to complete, unclear action buttons, unreliable access, and opaque password rules can often contribute to the churn. Creating a seamless user experience can help your company stand out.
SMS, magic link, and Touch ID are three passwordless techniques to consider in order to facilitate a smooth account access process.
- SMS takes a phone number, avoiding any need for the user to enter an email
- Magic link only requires the email address for users to click and authenticate
- Biometrics, such as TouchID detect your thumbprint
In each case above, sign-up is simplified and offers a consistent user experience once the account is created. In turn, this drives an improved engagement level and matches customer expectations gained from other leading platforms and services.
From a security perspective, passwordless authentication helps to mitigate bad customer practices such as weak passwords or choosing the same password for multiple accounts.
3. Give customers confidence that access is secure
We have already seen the huge rise in cybercrime and data breaches in our graphics above. Choosing the right CIAM solution helps to mitigate the risk of a fine resulting from a leak or security system being compromised.
For example, introducing Multi-Factor Authentication (MFA) increases your users' perception of security, and it is known that MFA offers excellent success levels for keeping breaches down mainly because it avoids dependency purely on passwords. Studies in 2017 found that breached passwords were the source of 81% of data breaches (up from 66% in 2016).
Customer Identity Management Summary
The sharp rise in customer expectations and online transactions means that customer identity is now a key success factor for any business, service, or platform to focus on. Choosing a CIAM solution, such as Okta or Auth0, to help meet the requirements for today as well as tomorrow is proving to maximise ROI as well as comply with ever-changing compliance and user security policies.
Check out our articles like Okta Workflows For Customer Identity.